
Why Big Tech shreds millions of storage devices it could reuse
Oct 7
A recent Financial Times longread delves into datacenter storage use, e-waste, data security and Big Tech’s reuse practices (or lack thereof). We share a related tech tip for the rest of us.

The ABC’s of Cybersecurity
May 30
Not so long ago we were all anxiously biting our nails over the impending threat of the WannaCry cyberattack, which affected over 300,000 computers worldwide. Even though the ransomware attack was resolved in a matter of days, it swiftly incurred billions of dollars in damages. The reality is, it hasn’t been too long since this major attack, and threats to your own cybersecurity measures are as prevalent now as they were then. It’s important to take precautions when it comes to protecting confidential corporate information, but just what do those precautions entail?

International Data Privacy Day: Strong, Sensitive, Secure
Jan 25
While the majority of North Americans were asking Santa for new tech, we were busy building a contingency plan to protect our existing devices. In December, we were all wishing for things. In January, it’s time to take action to protect our technology and sensitive data from prying eyes, ears, and keyboards.

Equifax: Zero Credit for Poor Handling of Massive Data Breach
Sep 26
“Based on the information provided, we believe that your personal information may have been impacted by this incident.”
Sound familiar? You and 143 million other people in the United States, the UK, and Canada.That’s right – Americans weren’t the only ones affected by the massive Equifax data breach.
It’s been quite a year for data breaches (many a result of escalating and evolving ransomware), but this situation was largely precipitated by Equifax’s negligence. Companies who feel they are taking extensive preventative measures can always do more. Being on the defense is not the same as mounting an offense.

Back-to-School, Back to Secure: Security Best Practices for All Age Groups
Aug 17
Whether it’s coming to a grinding halt or a gradual slowdown, there’s no doubt about it: summer is approaching its end. But while the temperatures are decreasing, hackers are increasing their efforts targeting networks and users of all ages. Cyberattacks span payment card fraud, unintended disclosure, hacking, malware, insider leaks, and ransomware—these are only a few of the most common approaches.
Different age groups vary in online behavior and thus, are susceptible to different online scams, threats, and pitfalls. Understanding risk factors is the first step toward protecting yourself.
WannaCrypt: The Ransomware That Makes You Wanna Cry
May 19
Ransomware isn’t new, but it’s been all over the news recently. Just last weekend, hackers launched a massive cyberattack that crippled hundreds of thousands of computers around the globe. Known as WannaCrypt—also called WannaCry or Wanna Decryptor—it is a particularly damaging brand of virus known as ransomware.

You Shall Not Pass: The 10 Commandments of Password Protection
Sep 21
Lists confirm it: we are lazy when creating passwords. The sheer number of accounts, applications, and devices we own almost guarantees poor password quality. Employ these tips and best practices to fortify and protect your numerous accounts and devices.

The Rise of Ransomware: How to Handle Data Hijacking
May 16

Ransomware is all the rage—and not in a good way. Cybersecurity experts are calling these virtual attacks an ‘epidemic’ of epic proportions.
In fact, its exponential growth over the past few years has left individuals, companies, and industries feeling both enraged and powerless.
Why? Well, because the only protection against ransomware is caution.

The Hidden Hazard: Protecting Your Organization from Insider Threats
Feb 8

Threats to the security and safety of your data are all around. Many people are familiar with the most common Internet dangers, such as Phishing scams, stolen passwords, browser vulnerability, and hackers. However, there’s another, more duplicitous danger at work. In recent years, Insider Threats have become a huge Cybersecurity concern.

Lessons on Data Safety from the Ashley Madison Hack
Sep 10
 No matter what your stance on the Ashley Madison cyberattack or where your interest lies, there is one important lesson that everyone should be taking from the incident: your data is not as safe as you think it is. The apparent vulnerability of sensitive data submitted online is cause for alarm and serious consideration.
No matter what your stance on the Ashley Madison cyberattack or where your interest lies, there is one important lesson that everyone should be taking from the incident: your data is not as safe as you think it is. The apparent vulnerability of sensitive data submitted online is cause for alarm and serious consideration.

Cybersecurity Threats Are Always Evolving
Jun 12
No Target Unturned.

It’s a connected digital world and as far as information technology goes threats from hackers to our data are always prevalent and evolving. Break-ins to computer systems have put IT departments on guard for data theft and espionage for years. One new corporate sector target is becoming a clear favorite for cybercriminals though. According to security firm research – the energy industry is now the sector with the highest number of reported attacks.
High-Profile Data Destruction: Snowden Hard Drives Destroyed by Guardian Editors
Jan 31

Back in July during peak moments of the Edward Snowden leak scandal explosion around the world, the UK’s Guardian newspaper was embroiled in a battle with government about the information in the paper’s possession. Government officials and the GCHQ spy agency threatened injunctions against the paper. Finally staff decided they had to destroy all the computers to prevent their journalists being carted away and measures being taken against the paper.
See footage of the destruction after the jump

Data Safety Archive: Photocopiers Potential Security Risk
Mar 27
 Ever thought about all the information that passes through your office copy machine? Here’s a good look at one place where the security of your personal information is threatened.
Ever thought about all the information that passes through your office copy machine? Here’s a good look at one place where the security of your personal information is threatened.
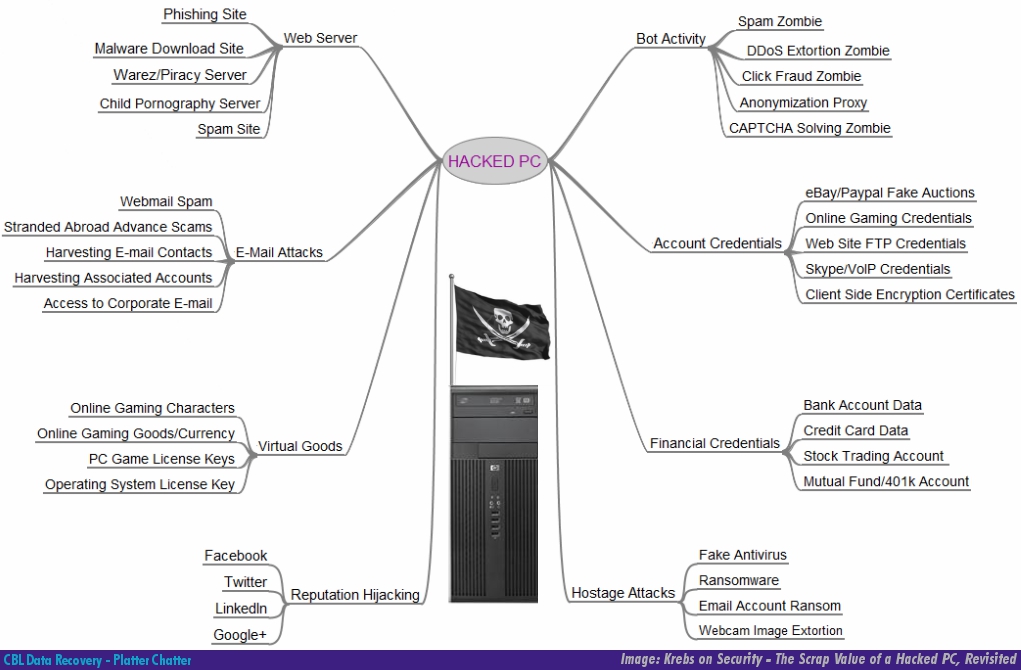
Data Safety: The Value of Your Data to a Hacker
Oct 18
We’ve talked about data safety and protection before. Besides the destruction of information from crashes and deletion, threats to your data’s safety come in the form of threats to its security, and that affects your privacy.
Tech columnist Brian Krebs has a great article where he tries to tackle the challenge of explaining why a hacker would want to get into your PC. What’s interesting is that most of the items listed are some sort of data or personal information.


Canadian Privacy audit finds breach at Staples: laptops resold with customer data
Jun 21
Staples Business Depot, the office supplies store chain, was fingered by the office of Canada’s Privacy Commissioner in a recent report. The report details findings that Staples was reselling returned laptops and digital devices without properly wiping customer data off them.

New Jersey Hard Drive Data Security Breach A Reminder to Us All
Mar 11
 When the State of New Jersey was preparing to put a bunch of old computer equpiment up for auction to the public, it didn’t realize it was about to auction off the private data of members of that public. State Comptroller Matthew Boxer was reviewing the sale of hundreds of computers that is a usual occurrence in the state office when he discovered that the “hard drives in 79% of the machines had tons of private data on them” still! The sale was stopped thanks to the auditor’s investigation, but there is little doubt that the state had already been selling computers with confidential data on them for some time.
When the State of New Jersey was preparing to put a bunch of old computer equpiment up for auction to the public, it didn’t realize it was about to auction off the private data of members of that public. State Comptroller Matthew Boxer was reviewing the sale of hundreds of computers that is a usual occurrence in the state office when he discovered that the “hard drives in 79% of the machines had tons of private data on them” still! The sale was stopped thanks to the auditor’s investigation, but there is little doubt that the state had already been selling computers with confidential data on them for some time.

Your Privacy: How Safe Is Your Data? (Part 5)
Feb 15
 While the cost of a new computer or laptop continues to fall, we truly are almost in an age when these former room-sized giants are now disposable. When last year’s speed-demon is today’s dinosaur, and the cost and hassle of upgrading and updating is on par with simply buying new, what happens to your beloved old digital friend?
While the cost of a new computer or laptop continues to fall, we truly are almost in an age when these former room-sized giants are now disposable. When last year’s speed-demon is today’s dinosaur, and the cost and hassle of upgrading and updating is on par with simply buying new, what happens to your beloved old digital friend?
(Part 5 of our series on Data Safety)
Worrying About Your Data
Aug 18
More and more computer users are becoming aware of a growing amount of data privacy issues around us. Protecting your personal data should be a top priority given the alarming increase in identity theft. This is leading people to worrying about what happens to their personal information and who’s hands it can fall into. CBL offers some tips and options for securely disposing of old storage devices.