
Why Big Tech shreds millions of storage devices it could reuse
Oct 7
A recent Financial Times longread delves into datacenter storage use, e-waste, data security and Big Tech’s reuse practices (or lack thereof). We share a related tech tip for the rest of us.

The Grinch Wants Your Data: Holiday Shopping Do's & Don'ts
Nov 29
Shopping of all sorts is making a comeback after the impacts of the COVID-19 pandemic and Black Friday and Cyber Monday remain at the center of the season. Being back in the habit is a blend of in-store and online shopping now. Where there are deals, there are cybersecurity threats. While more consumers are aware of the weaknesses and data breaches out there, the number of attack vectors out there continues to rise and hackers are there to take advantage. When you’re out and online looking for discounts and deals, protect yourself from Grinches that want to get ahold of your data with these tips.

Vulnerability in Connected Western Digital My Book Live Drives Threatens to Wipe Data of Unsuspecting Owners
Jun 25
A critical vulnerability in some WD My Book Live external drives caused some owners to find their data had be wiped by a remotely run command. Western Digital’s only recommendation in the wake of customer complaints and alarm was to unplug the devices from the internet to disconnect them from being compromised.
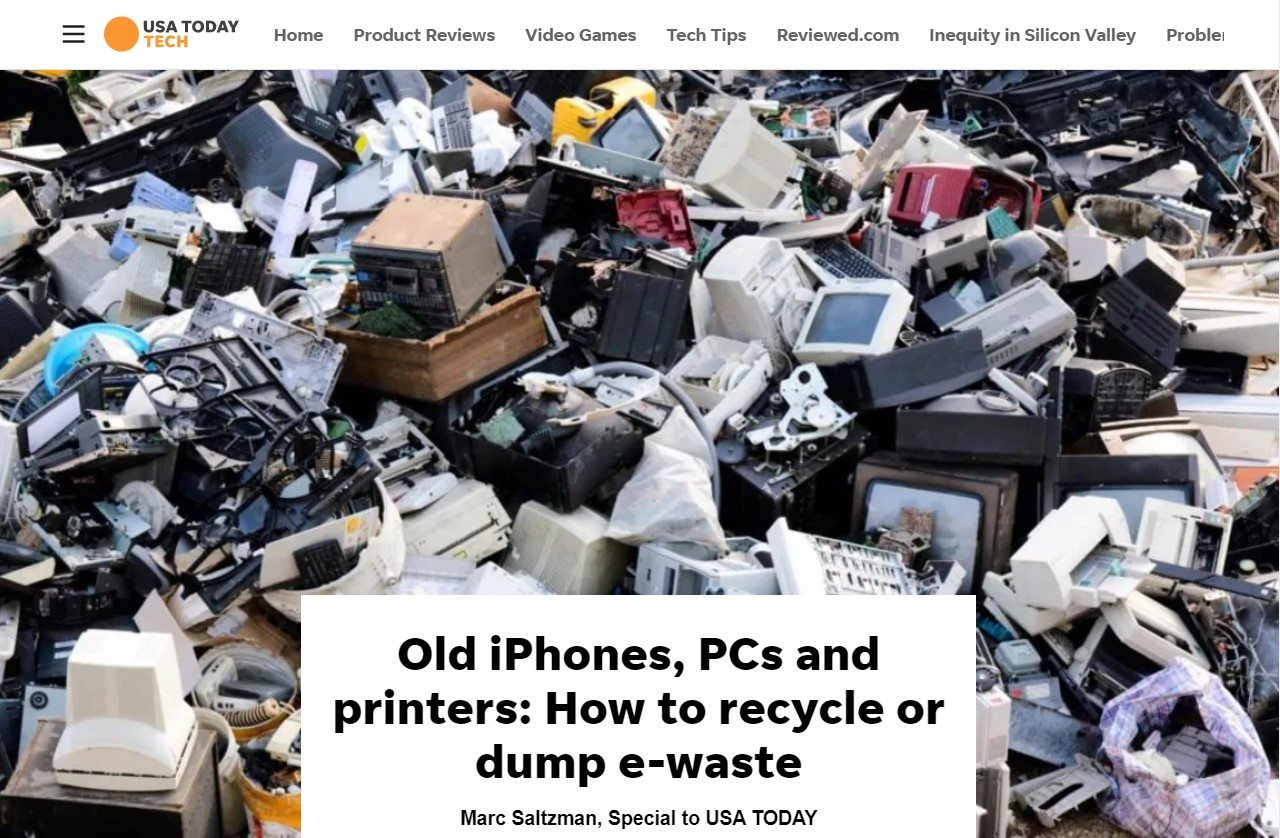
On the E-Waste Case: USA Today #TechTip
May 31
In an article about recycling devices and the challenges of e-waste, USA Today mentioned a good tech tip about data erasure to protect your privacy.
More Electronics, More Data, More E-Waste
Apr 22
The occasion of Earth Day is a good time to reflect on how much e-waste we’re creating and its effect on our environment, health, and even our data.

Spring Ahead and Look Towards the Future of Storage
Mar 18
Spring is the season for new beginnings so let’s look at how new applications with new requirements and breakthrough storage technologies will bring fresh approaches to the ways we use and store our data.

Study: Wide Array of Private Data on Secondhand Drives, a Reminder to Discard With Discretion
Oct 15
Researchers at the University of Hertfordshire performed a study examining secondhand hard disk drives and found they often contained data from their previous owners.

Data Prep Tips for Back-to-School/Work
Aug 30
As temperatures start to slowly drop, students and employees are emerging from a summer daze, hunkering down for the school year and getting get business in shape for the fall season. Here’s 3 ways you can get data-ready for back-to-school & back-to-work.

Art Exhibit Focuses on E-Waste Data Dangers
Jun 6
A duo of artists known as KairUs curious about private data breaches and e-waste created an exhibition of artworks entitled “Forensic Fantasies”. Highlighting some key issues and effects related to e-waste dumps in places like Ghana, a topic we’ve covered before, they look at some interesting intersections of technology, the environment, and society.

The ABC’s of Cybersecurity
May 30
Not so long ago we were all anxiously biting our nails over the impending threat of the WannaCry cyberattack, which affected over 300,000 computers worldwide. Even though the ransomware attack was resolved in a matter of days, it swiftly incurred billions of dollars in damages. The reality is, it hasn’t been too long since this major attack, and threats to your own cybersecurity measures are as prevalent now as they were then. It’s important to take precautions when it comes to protecting confidential corporate information, but just what do those precautions entail?

International Data Privacy Day: Strong, Sensitive, Secure
Jan 25
While the majority of North Americans were asking Santa for new tech, we were busy building a contingency plan to protect our existing devices. In December, we were all wishing for things. In January, it’s time to take action to protect our technology and sensitive data from prying eyes, ears, and keyboards.

6 Practical and Essential Data Safety Items to Put on Your Wishlist (And Check Twice)
Dec 20
Our tech support and data recovery specialists have assembled a practical wish list for your cyber safety, so you can have the most wonderful time all year, every year (approved by The Big Guy, himself).

The Gift That Keeps on Giving: 5 Critical Changes to Cybersecurity Policy
Nov 29
2017 has been a particularly bad year for data debacles and cybersecurity breaches. Fortunately, federal and state governments, and companies—large and small—recognize that lasting, legislative change is required to prevent future cyber attacks and protect everyone’s data.
As we enter the season of giving, here’s what governments and businesses are offering to remedy past mistakes. The gift that keeps on giving? Progress in the form of policy change.

October: National Cybersecurity Awareness Month
Oct 24
Self-driving cars. Artificial intelligence. Smart home technology. Voice-activated home assistants. Virtual reality. The stuff of popular science fiction is no longer fiction. The future isn’t ahead; it’s already here.
Once again, it’s National Cybersecurity Awareness Month (NCSAM).

Equifax: Zero Credit for Poor Handling of Massive Data Breach
Sep 26
“Based on the information provided, we believe that your personal information may have been impacted by this incident.”
Sound familiar? You and 143 million other people in the United States, the UK, and Canada.That’s right – Americans weren’t the only ones affected by the massive Equifax data breach.
It’s been quite a year for data breaches (many a result of escalating and evolving ransomware), but this situation was largely precipitated by Equifax’s negligence. Companies who feel they are taking extensive preventative measures can always do more. Being on the defense is not the same as mounting an offense.

Back-to-School, Back to Secure: Security Best Practices for All Age Groups
Aug 17
Whether it’s coming to a grinding halt or a gradual slowdown, there’s no doubt about it: summer is approaching its end. But while the temperatures are decreasing, hackers are increasing their efforts targeting networks and users of all ages. Cyberattacks span payment card fraud, unintended disclosure, hacking, malware, insider leaks, and ransomware—these are only a few of the most common approaches.
Different age groups vary in online behavior and thus, are susceptible to different online scams, threats, and pitfalls. Understanding risk factors is the first step toward protecting yourself.

Speeding Up or Slowing Down?: 7 Cybersecurity Startups to Watch in 2017
Jul 21
Overall, a previously burgeoning startup marketplace has been in decline since 2016. Dark Reading cites the startup slowdown a result of reduced funding from venture capital firms. However, one industry continues to boom, despite the overall decline: cybersecurity.

Amazon Goes Grocery Shopping, Buys Whole Foods
Jun 23
More and more, businesses are looking for ways to blend brick-and-mortar stores with online services. The company that rules the online marketplace? Amazon. But Bezos is branching out.
WannaCrypt: The Ransomware That Makes You Wanna Cry
May 19
Ransomware isn’t new, but it’s been all over the news recently. Just last weekend, hackers launched a massive cyberattack that crippled hundreds of thousands of computers around the globe. Known as WannaCrypt—also called WannaCry or Wanna Decryptor—it is a particularly damaging brand of virus known as ransomware.

Loves Me, Loves Me Not: 4 Sweetheart Scams to Avoid This Valentine’s Day
Feb 13
With Data Privacy Day and Safer Internet Day behind us and Valentine’s Day just ahead, it’s time to take what we learned and apply it.

7 Security Resolutions for 2017
Jan 16
The New Year carries the promise of infinite potential. Yet again, individuals are engaging in the common practice of resolution-making. But the percentage of people who see these resolutions through to conclusion is shockingly low.
The proliferation of technology has made time more precious than ever. Our lives move faster, so we need to accomplish more in a shorter period of time. We’d like to offer 7 security resolutions that you should make — and achieve — in 2017.

Piling Up - Pictures give a glimpse of e-waste recycling challenges
Oct 21

As the landfills pile up around the world, how safe is it for our discarded tech to end up in e-waste ‘mountains’?
This gallery of pictures from The Guardian gives a brief visual glimpse of the challenges of e-waste recycling and global efforts to reduce waste focusing on recycling operations in Guiyu, China.

October is National Cybersecurity Awareness Month
Oct 19
“In 2016, there have been 454 data breaches with nearly 12.7 million records exposed.”
If this statistic doesn’t scare you, it should.
October is dominated by Halloween: pumpkin carving, cider drinking, costume searching, candy eating, and Trick-or-Treating. Most people don’t realize that October is shared by another important event: National Cybersecurity Awareness Month.

You Shall Not Pass: The 10 Commandments of Password Protection
Sep 21
Lists confirm it: we are lazy when creating passwords. The sheer number of accounts, applications, and devices we own almost guarantees poor password quality. Employ these tips and best practices to fortify and protect your numerous accounts and devices.

Pokémon No-Go: What’s the Catch?
Jul 15
The mobile app, Pokémon Go, is a global phenomenon.
 Comfortably seated at No. 1 on mobile download charts for both iOS and Android users, the app has made virtual reality mainstream, prompting users to get off the couch and go explore the real world, but through a virtual lens.
Comfortably seated at No. 1 on mobile download charts for both iOS and Android users, the app has made virtual reality mainstream, prompting users to get off the couch and go explore the real world, but through a virtual lens.
However, people can collect a lot more than Pokémon.
We break down the basics of the game and look into some potential risks and threats to your data privacy, cybersecurity and more.

The Rise of Ransomware: How to Handle Data Hijacking
May 16

Ransomware is all the rage—and not in a good way. Cybersecurity experts are calling these virtual attacks an ‘epidemic’ of epic proportions.
In fact, its exponential growth over the past few years has left individuals, companies, and industries feeling both enraged and powerless.
Why? Well, because the only protection against ransomware is caution.

Spring Into Action: Top 5 Do's & Don'ts of Data Cleanup
Apr 19

“April showers bring May flowers,” as they say. April also brings with it the frenzy of spring cleaning. This is the time of year when everything must sparkle, fit neatly into its predetermined spot, or go curbside. Everywhere and everything is fair game: your home, your garage, the interior and exterior of your car, your fridge, your office, and…your data.
Just like the clutter in your closet or garage, your data can be disorganized, old, poor quality, or redundant. Fortunately, de-cluttering your data will make your life (and business) run more smoothly in the long-term.

How to Demolish Old Hard Drive Data (keeping your data safe, the logical way)
Mar 24

If you have a computer that you are getting rid of you need to take special care of the data you have stored inside it. Whatever information you have saved on the hard drive inside: photos, documents, financial files, passwords, emails — personal information, does not simply go away if you hit delete or drop stuff in the Recycle Bin.
Ben Popken at NBC did a video showing some low-tech solutions to this problem. He trashes hard drives with everything from hammers and baseball bats, to submerging in water and burning with fire. Watch the video after the jump.

Data Disasters: When a Big Data Loss Becomes a Giant Problem
Mar 16

Filing cabinets and safety deposit boxes are old-school. In this technological age, our personal, most valuable information is secured somewhere in the digital universe. It might be saved on an external hard drive or on an internal server. It might live in the Cloud, in an encrypted file, or in a Dropbox folder. Wherever your data is located, there’s no way to be sure it’s 100% safe or secure.
Disaster is inevitable. Sometimes it’s a fender bender or a stolen credit card. Other times, it’s a Big Data disaster.
What is Big Data?
Big Data is a recent ‘hot topic’ in the tech world. It is:
“A term that describes the large volume of data – both structured and unstructured – that inundates a business on a day-to-day basis. But it’s not the amount of data that’s important. It’s what organizations do with the data that matters. Big data can be analyzed for insights that lead to better decisions and strategic business moves.”
The second part of this definition is the critical piece; it’s not the amount of data, but what can be done with the data.

The Hidden Hazard: Protecting Your Organization from Insider Threats
Feb 8

Threats to the security and safety of your data are all around. Many people are familiar with the most common Internet dangers, such as Phishing scams, stolen passwords, browser vulnerability, and hackers. However, there’s another, more duplicitous danger at work. In recent years, Insider Threats have become a huge Cybersecurity concern.

Tips for Secure Online Shopping
Dec 9

Increasingly more people are opting to do their holiday shopping online rather than subject themselves to the chaos of crowded malls this time of year. Saving people time and energy over the hectic holiday season is no doubt a great benefit brought by the evolution of the internet, but it doesn’t come without its own unique set of evils.
Recent incidents of cybersecurity and data theft have brought light to the risks consumers face when sharing and entrusting their sensitive data with corporations and third party institutions. Malicious intentioned cyber criminals continue to develop new, tech-savvy ways to hack into people’s private accounts for the purpose of stealing sensitive information.
Protect your data while doing your holiday shopping online this month with these tips and safety precautions.

Lessons on Data Safety from the Ashley Madison Hack
Sep 10
 No matter what your stance on the Ashley Madison cyberattack or where your interest lies, there is one important lesson that everyone should be taking from the incident: your data is not as safe as you think it is. The apparent vulnerability of sensitive data submitted online is cause for alarm and serious consideration.
No matter what your stance on the Ashley Madison cyberattack or where your interest lies, there is one important lesson that everyone should be taking from the incident: your data is not as safe as you think it is. The apparent vulnerability of sensitive data submitted online is cause for alarm and serious consideration.

Cybersecurity Threats Are Always Evolving
Jun 12
No Target Unturned.

It’s a connected digital world and as far as information technology goes threats from hackers to our data are always prevalent and evolving. Break-ins to computer systems have put IT departments on guard for data theft and espionage for years. One new corporate sector target is becoming a clear favorite for cybercriminals though. According to security firm research – the energy industry is now the sector with the highest number of reported attacks.
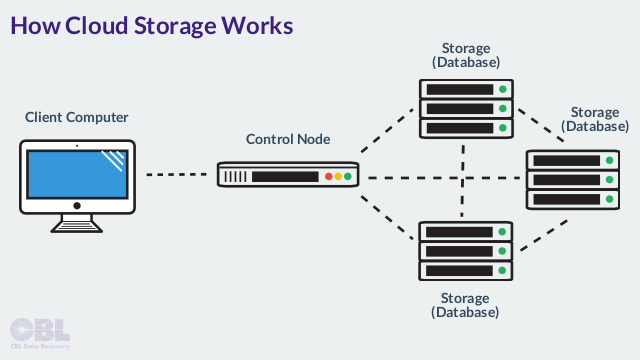
Where Is Cloud Data Actually Stored?
Feb 25

With the rise in popularity of cloud-based data storage, more people are asking where and how information is actually stored by cloud providers. More precisely, what exactly is the ‘cloud’, and how secure is storing and sending information through the virtual network? It’s important to have a basic understanding of how your information is being handled–particularly the aspects of a service provider that you should be cognizant of in order to ensure the safety and privacy of your data.

EHR Data Safety Threat Is Real - Clerk Charged with Selling Patient Info
Nov 26
In a rush to modernize and increase technological access sometimes the looming threats to privacy and safety of personal healthcare information are not given as much attention. A recent story exemplifies a growing real threat.

Your Data, Your Electronics, Our E-Waste
Apr 22
On the occasion of Earth Day, we reflect on a lurking issue – E-Waste. Often underestimated in size, global technological growth also produces an amazing amount of waste annually. When you think about the amount of devices that you have gone through, from PC hard drives to cellphones, and then multiply it by your neighborhood, city, country….where do all those electronics go?
High-Profile Data Destruction: Snowden Hard Drives Destroyed by Guardian Editors
Jan 31

Back in July during peak moments of the Edward Snowden leak scandal explosion around the world, the UK’s Guardian newspaper was embroiled in a battle with government about the information in the paper’s possession. Government officials and the GCHQ spy agency threatened injunctions against the paper. Finally staff decided they had to destroy all the computers to prevent their journalists being carted away and measures being taken against the paper.
See footage of the destruction after the jump
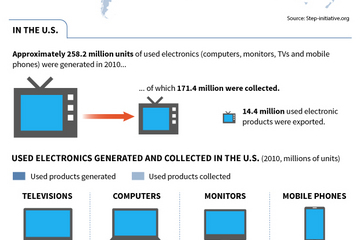
E-waste On The Move
Dec 18
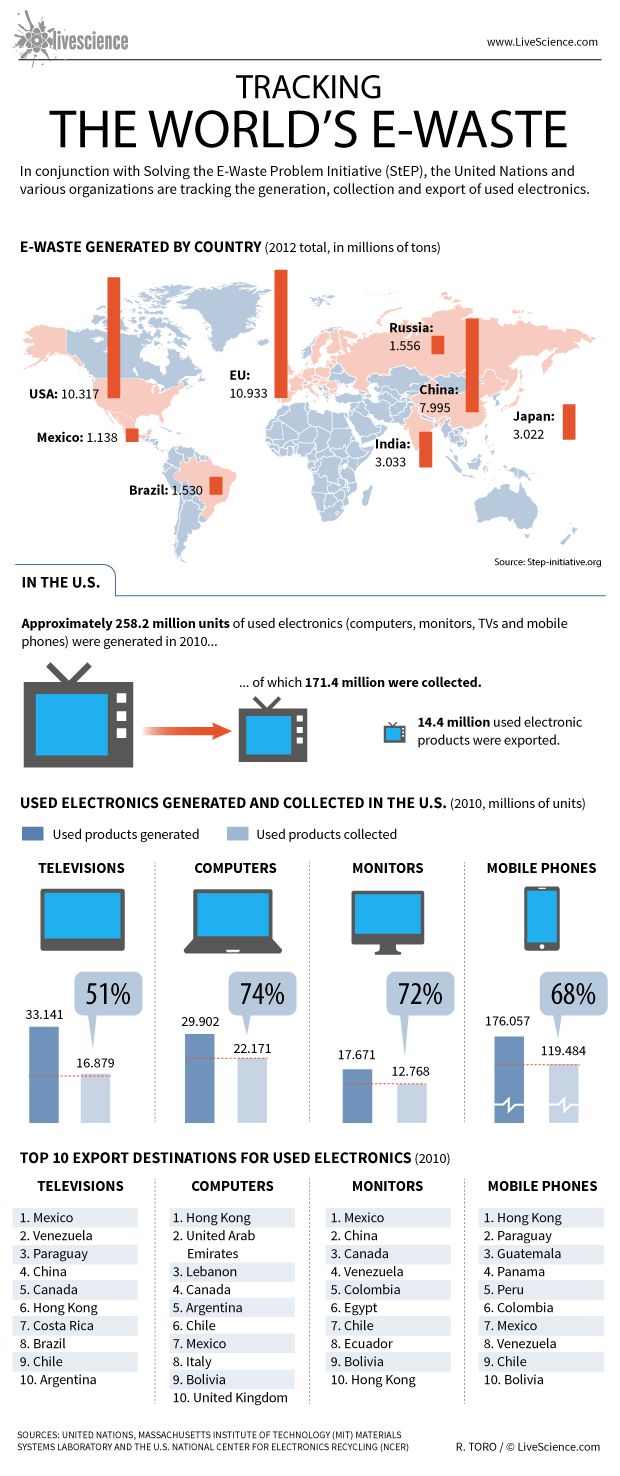 New report numbers out of the United Nations’ StEP Initiative proclaim e-waste as one of the world’s fastest growing streams of waste production. StEP(Solving The world’s E-waste Problem) was set up to tackle the growing and often underestimated problem of electronic waste. According to figures, last year 50m tons of e-waste was generated. This is following the predicted trend that in the next four years e-waste will grow 33%.
New report numbers out of the United Nations’ StEP Initiative proclaim e-waste as one of the world’s fastest growing streams of waste production. StEP(Solving The world’s E-waste Problem) was set up to tackle the growing and often underestimated problem of electronic waste. According to figures, last year 50m tons of e-waste was generated. This is following the predicted trend that in the next four years e-waste will grow 33%.

Video: E-wasteland
Jul 25
 Used electronic devices are often discarded in the cheapest way possible to some of the world’s poorest countries. Watch a recent TV report on location in Ghana that gives a glimpse into the conditions of the scrap yard/slums that e-waste is being collected and dumped in.
Used electronic devices are often discarded in the cheapest way possible to some of the world’s poorest countries. Watch a recent TV report on location in Ghana that gives a glimpse into the conditions of the scrap yard/slums that e-waste is being collected and dumped in.
Electronics Recycling in Ontario - E-Cycling!
Jul 12
The mountain of electronics we have and eventually need to get rid of is always growing. The need to dispose of old electronics like cellphones and tvs as well as computer hardware in laptops and desktops shows no sign of slowing. But that does present some challenges with regards to how to minimize the amount of e-waste we produce as well as the impact and threat to sensitive information.
The movement to promote E-cycling is strong in Ontario, Canada.
Check out this promo video about drop-off locations:
When you drop-off an old computer for e-cycling, what information is still on the hard drive inside it? We made CBL Data Shredder for this sole purpose. Keep reading to find out more.

E-Waste Recycling up 53 Percent - Remember to Wipe those Drives
Apr 19
 Good news this week comes in an update from the Consumer Electronics Association on their ‘eCycling’ initiative reporting a big increase in electronics recycling – up 53% in the past year! Are you one of the growing number of people that are seeking out drop-off locations for used computers and electronics? Be reminded that you should wipe any hard drive before discarding or recycling it to protect yourself from any potential privacy threats or criminal activity.
Good news this week comes in an update from the Consumer Electronics Association on their ‘eCycling’ initiative reporting a big increase in electronics recycling – up 53% in the past year! Are you one of the growing number of people that are seeking out drop-off locations for used computers and electronics? Be reminded that you should wipe any hard drive before discarding or recycling it to protect yourself from any potential privacy threats or criminal activity.

Clip: CBL Data Shredder - Costco Tech Connection
Feb 8
 The only thing we love almost as much as getting back our customers’ data is preventing it from falling into the wrong hands. The privacy of your information and importance of protecting data is a crucial part of what we do and of our digital society today. Getting rid of old hardware is one challenge, but what about the files and data stored on computers? Friend of Platter Chatter and tech reporter extraordinaire, Marc Saltzman, recently highlighted some key points about safely deleting data in Costco Connection magazine.
The only thing we love almost as much as getting back our customers’ data is preventing it from falling into the wrong hands. The privacy of your information and importance of protecting data is a crucial part of what we do and of our digital society today. Getting rid of old hardware is one challenge, but what about the files and data stored on computers? Friend of Platter Chatter and tech reporter extraordinaire, Marc Saltzman, recently highlighted some key points about safely deleting data in Costco Connection magazine.

E-Waste and Security Threats exposed by Frontline
Jun 24
PBS Frontline aired a feature about the Digital Dumping Ground in Ghana where so-called e-waste is being dumped last night. The footage revealing, exposed not only the disastrous environmental and social impact the giant amounts of electronic equipment waste is having on Ghana, but also a further side-effect: the risk of unwiped data being discovered and used for criminal activity from discarded hard drives!

Old Hard Drives and Data Security
May 8
Recently researchers managed to get their hands on highly sensitive data off of an eBay auction. Several hard drives were purchased and the researchers were able to recover sensitive data from the hard drives.